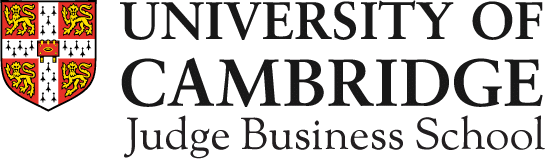Blockchain systems underpin trillions of dollars in digital assets and financial transactions. Quantum computing threatens the cryptographic foundations of these networks. The threat is not here yet, but quantum hardware and algorithms are progressing far faster than most anticipated.
Quantum machines now have over a thousand qubits, with much improved gate fidelities and error correction. Industry roadmaps aim for devices with thousands more qubits in the coming years. Preparing blockchain ecosystems for post-quantum cryptography (PQC) requires carefully coordinated upgrades in protocols, software and governance. This work must happen now, not when quantum computers are already breaking keys. The window for a smooth transition is rapidly narrowing.
The need to upgrade is more urgent for blockchains than for almost any other digital system, because of what is often called a ‘Harvest Now, Crack Later’ attack. In traditional finance, much of the data has a limited shelf life. In contrast, blockchain transactions are public and permanent. This allows an adversary to copy public keys from the blockchain today and simply wait for a quantum computer powerful enough to derive the private keys in the future. For blockchains, today’s vulnerabilities are permanent risks, making the switch to quantum-resistant security an immediate and critical priority.
The need to upgrade is more urgent for blockchains than for almost any other digital system.
Quantum vs blockchain cryptography
Quantum computing poses a threat to the digital signatures that protect blockchain assets. While components like Bitcoin’s proof-of-work mining remain relatively secure – as quantum search algorithms like Grover’s offer only a quadratic speedup that can be countered by protocol adjustments like increasing mining difficulty – the public-key cryptography that secures token ownership is fundamentally vulnerable. Algorithms like Shor’s[1] run on a powerful quantum computer, which can efficiently solve the hard mathematical problems (like discrete logarithms) that underpin signature schemes such as ECDSA and Ed25519. This would theoretically allow an attacker to derive a private key from a public one, forge signatures at will and steal assets. Because no amount of hashing power can prevent a fraudulent transaction signed with a compromised key, this quantum threat strikes directly at the core of identity and authenticity in blockchain systems.
This threat is not merely academic. Well-resourced, state-sponsored actors, often referred to as Advanced Persistent Threats (APTs), represent the most likely early adopters of this technology. These groups possess the long-term strategic focus and substantial funding necessary to utilise quantum capabilities for objectives such as undermining trust in global financial systems. For them, the ability to forge signatures on a major blockchain would be a powerful tool to illicitly fund operations or destabilise markets.
The majority of blockchain networks remain vulnerable. Table 1 provides a detailed breakdown of our review of the top 26 blockchain protocols, which reveals that 24 rely purely on quantum-vulnerable signature schemes. Industry leaders like Bitcoin and Ethereum use ECDSA, while other major platforms such as Solana, Cardano and Ripple use similar elliptic curve-based cryptography (EdDSA). All are vulnerable to a sufficiently powerful quantum computer running Shor’s algorithm. Only two projects in our analysis have begun meaningful experiments with quantum-safe signatures: Algorand is exploring hash-based signatures like SPHINCS+ and R3 Corda has experimented with lattice-based algorithms such as Dilithium. The case of IOTA is particularly telling: after pioneering a quantum-resistant signature scheme, the project reverted to the vulnerable Ed25519 standard in 2021, prioritising short-term performance over long-term security.[2] These projects remain the exceptions.
| Blockchain | Signature algorithm | Key size | Quantum-Resistant |
|---|---|---|---|
| Bitcoin | ECDSA (secp256k1) | 256-bit ECC | No |
| Ethereum | ECDSA (secp256k1) & BLS12-381 | 256-bit & 381-bit ECC | No |
| Cardano | Ed25519 | 256-bit ECC | No |
| Solana | Ed25519 | 256-bit ECC | No |
| Polkadot | Sr25519 & Ed25519 | 256-bit ECC | No |
| Binance Smart Chain | ECDSA (secp256k1) | 256-bit ECC | No |
| XRP Ledger | ECDSA (secp256k1) & Ed25519 | 256-bit ECC | No |
| Avalanche | ECDSA (secp256k1) | 256-bit ECC | No |
| Cosmos | Ed25519 | 256-bit ECC | No |
| Algorand | Ed25519 (Falcon planned) | 256-bit ECC | Planned/partial |
| Tezos | Ed25519, secp256k1, P-256, BLS | 256-bit ECC | No |
| Stellar | Ed25519 | 256-bit ECC | No |
| NEAR Protocol | Ed25519 & secp256k1 | 256-bit ECC | No |
| Polygon (PoS) | ECDSA (secp256k1) & Ed25519 | 256-bit ECC | No |
| Hedera | Ed25519, secp256k1, RSA-3072, P-384 | 256/384-bit ECC, 3072-bit RSA | No |
| IOTA | Ed25519 | 256-bit ECC | Discontinued |
| EOS | ECDSA (secp256k1/secp256r1) | 256-bit ECC | No |
| Fantom | ECDSA (secp256k1) | 256-bit ECC | No |
| Klaytn | ECDSA (secp256k1) & BLS | 256-bit ECC | No |
| TON | Ed25519 | 256-bit ECC | No |
| Flow | ECDSA (P-256/secp256k1) | 256-bit ECC | No |
| Sui | Ed25519, secp256k1/P-256, BLS12-381 | 256/381-bit ECC | No |
| Aptos | Ed25519, secp256k1, BLS12-381 | 256/381-bit ECC | No |
| Hyperledger Fabric | ECDSA (P-256/P-384) | 256/384-bit ECC | No |
| R3 Corda | Ed25519, secp256k1, RSA-3072, SPHINCS-256 | 256-bit ECC, 3072-bit RSA | Planned/partial |
| WAX | ECDSA (secp256k1/secp256r1) | 256-bit ECC | No |
Quantum progress and timeline
While expert consensus places a cryptographically relevant quantum computer typically 10 to 20 years away, this forecast is far from certain and may be shortening. Data from institutions like the Global Risk Institute[3] reveals significant volatility in expert opinion. For instance, the perceived near-term threat peaked in 2021. The fluctuation suggests that a single breakthrough could rapidly accelerate the timeline, making it prudent to prepare for the threat to materialise sooner rather than later. Figure 1 illustrates how expert consensus on the quantum threat timeline has evolved over the past five years.
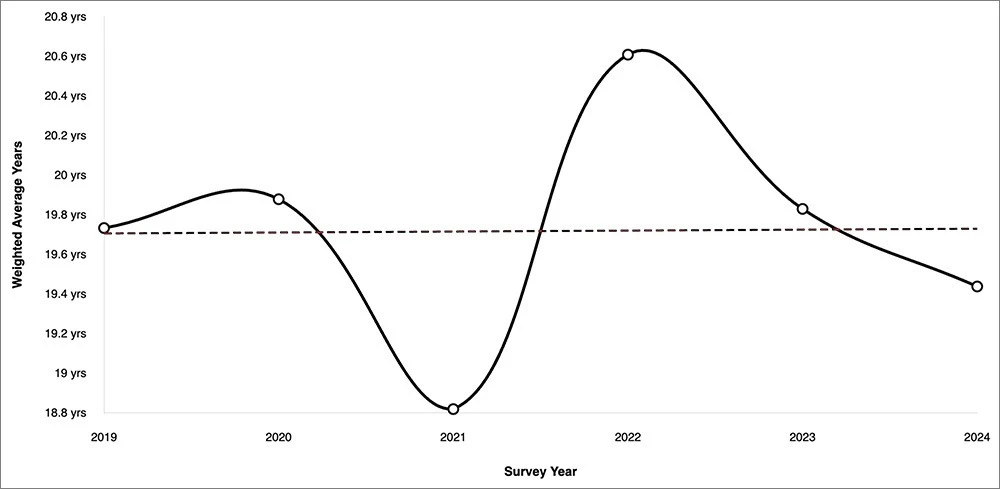
The substantial gap between current and required quantum hardware suggests we have years, but this timeline could compress dramatically. To break ECDSA or RSA, a fault-tolerant quantum computer needs anywhere from 1,700 to 25,000 logical qubits—that is, error-corrected qubits built from many physical qubits. For context, today’s cutting-edge processors are just crossing the thousand physical qubit threshold, and each logical qubit may require hundreds or even thousands of physical qubits depending on error rates. While IBM’s 133-qubit Heron chip[4] represents a milestone in quality, their 1,121-qubit Condor processor from late 2023 highlights the rapid progress in scale, though comprehensive benchmarks for it are still pending. Recent algorithmic breakthroughs have dramatically compressed these requirements. 2025 research[5] achieved a dramatic reduction in logical qubit requirements for breaking RSA-2048: approximately 1,399, pulling expert timelines forward significantly – what seemed decades away now appears potentially feasible within a decade. Figure 2 maps the current state of quantum computing hardware against the estimated requirements for breaking blockchain cryptography, showing where we are today relative to the threat threshold.
Qubit quality matters as much as qubit count, and quality is improving markedly faster than quantity. As shown in Figure 3 below, 2-qubit gate ‘infidelities’ (error probabilities) have been falling steadily.[6] Leading platforms now achieve >99.9% fidelity (1 error in 1000 operations),[7] a remarkable leap from just a few years ago. Lower error rates dramatically extend feasible computation time, which matters because attacking blockchain cryptography via Shor’s algorithm requires a long sequence of quantum operations.

One unexpected breakthrough could accelerate the threat timeline because quantum progress is decidedly not linear. Some technologists have already revised their estimates to the early 2030s based on recent milestones.[8] On the other hand, progress could stall due to stubborn engineering hurdles. Microsoft’s 2023 claim of evidence for ‘topological qubits’ sparked considerable interest but has yet to produce a working quantum computer.
Readiness gaps
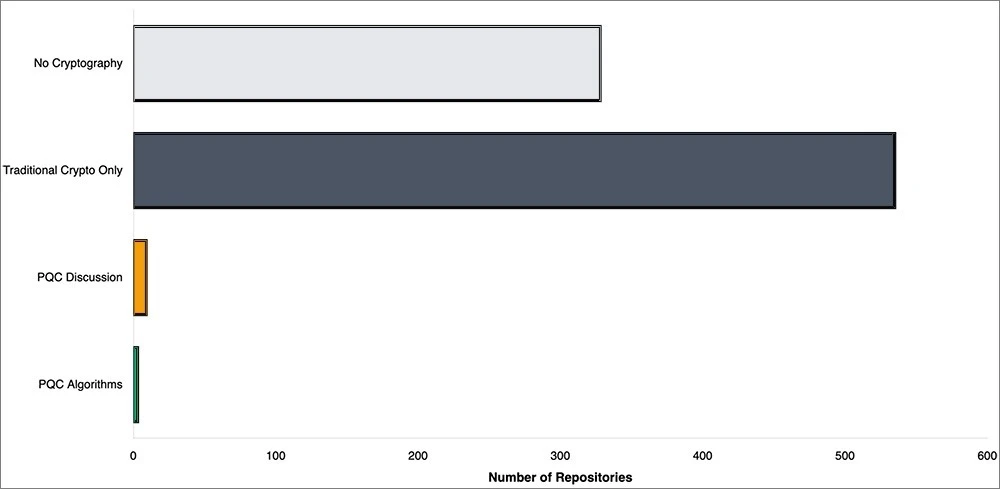
Given a timeline of 10-20 years, how prepared are blockchain networks and developers for quantum computing? We at the Cambridge Centre for Alternative Finance[9] analysed blockchain code on GitHub,[10] examining 879 repositories across major blockchain ecosystems for cryptography use and quantum-resistant techniques. The results show a gap between awareness and action. Of the 879 blockchain repositories analysed, 550 repositories (62.6%) contain cryptographic code including hashing, key generation and digital signature libraries. Yet only 14 repositories (1.6%) reference post-quantum cryptography in any form. Of these 14, only 4 repositories (0.5%) reference actual post-quantum algorithms such as Dilithium, SPHINCS+, NTRU, or Falcon. The remaining 10 repositories contain only generic discussion terms like ‘quantum-resistant’ or ‘post-quantum’ in documentation or comments, with no concrete implementations. Figure 4 visualises the gap between blockchain repositories using cryptography and those implementing post-quantum algorithms.
As illustrated in Figure 5, a timeline analysis of 1,725 cryptography adoption events from 2004 to 2025 further illustrates the dominance of traditional cryptography and virtual absence of quantum-safe alternatives. Traditional cryptographic algorithms account for 1,702 events (98.7%), while post-quantum algorithms appear in only 6 events (0.35%). Generic post-quantum discussion terms appear in 17 events (0.99%), primarily in conference transcripts, Bitcoin Improvement Proposals (BIPs) and Ethereum Improvement Proposals (EIPs). The first post-quantum algorithm mention appeared in 2018 with Dilithium, followed by scattered references to SPHINCS+ and NTRU in 2021. Even in 2025, actual PQC algorithm adoption remains negligible.

While blockchain networks show minimal quantum-resistant preparation, major financial institutions are rapidly increasing their exposure to public blockchains. BlackRock’s BUIDL fund,[11] launched in March 2024 on Ethereum, represents the world’s largest tokenised money market fund with over $1.5 billion in assets. Standard Chartered’s CEO Bill Winters declared in November 2025 that “pretty much all transactions will settle on blockchains eventually,”[12] signalling a complete rewiring of global finance. Industry projections suggest tokenised real-world assets will reach $2 trillion by 2028.[13] This trajectory matters more than current exposure: while banks have minimal operational exposure to public blockchains today, the rapid adoption of tokenised assets on quantum-vulnerable networks like Ethereum and Bitcoin creates future risk.

Figure 6 shows the evolution of Bitcoin’s quantum-vulnerable holdings:[14] 3 to 5 million BTC (14-24% of the total supply) stored in vulnerable ways. This includes coins in Pay-to-PubKey (P2PK) addresses from Bitcoin’s launch that directly expose public keys on-chain, plus coins in reused addresses where public keys have been revealed by spending. Ethereum may be even more exposed due to its account model. Any Ethereum address that has sent a transaction inevitably reveals its public key in the signature. The majority of Ether currently in circulation would be vulnerable if quantum day arrived now. Without timely mitigation, a quantum computer in the next decade could realistically jeopardise tens if not hundreds of billions in cryptoassets across multiple blockchains.
Toward quantum-resilient blockchains: technical and policy solutions
The challenge has 2 distinct parts: deploying quantum-resistant cryptography and doing so in a way that maintains decentralised network functionality. How can the blockchain community effectively quantum-proof itself?
Solutions are actively emerging on the technical front. NIST has finalised post-quantum cryptography standards,[15] including digital signature algorithms based on mathematical problems believed resistant to quantum attacks. Examples include lattice-based schemes like CRYSTALS-Dilithium and Falcon, and hash-based schemes like SPHINCS+. Blockchain developers are already testing these in labs and testnets. The real task is integrating them seamlessly into blockchain protocols through new address types or transaction formats that use post-quantum signatures instead of ECDSA.
Ethereum’s account abstraction approach offers a promising model for gradual migration. Via account abstraction, Ethereum plans to allow flexible verification routines for accounts. Users could then opt to use a post-quantum signature scheme for their wallet. Ethereum co-founder Vitalik Buterin has explicitly cited[16] “switching to quantum-resistant cryptography and rotating out old keys” as motivation for account abstraction in future protocol phases. This would enable rolling out PQC first as optional, then eventually mandatory.
Other blockchains are actively exploring hybrid approaches and migration mechanisms. Cardano has explored adding hybrid signatures that combine classic and PQC signatures to secure funds during a transition. Bitcoin developers have proposed concepts like Quantum-Resistant Address Migration to proactively move coins to quantum-safe addresses before an attack can happen. Bitcoin’s notoriously conservative governance makes such a hard fork contentious, but the proposal reflects growing awareness that doing nothing is simply not an option.
However, technical solutions are only half the battle. The transition to quantum-safe cryptography is both a technical feat and a significant governance challenge that requires ecosystem-wide co-ordination. All nodes in a network must agree to recognise new algorithms, a process that can take years of patient education and consensus-building, as past network upgrades have shown. Backwards compatibility is another critical consideration, as new quantum-safe addresses will coexist with old ones, requiring carefully designed mechanisms to retire legacy keys. Ecosystem leaders – from foundations to core developer teams – must champion quantum readiness as a strategic priority.
User practices and operational measures can provide interim protection but are not permanent solutions. Users and custodians can mitigate some risk by not reusing addresses, keeping public keys carefully hidden until needed. Organisations holding cryptocurrency should systematically inventory their exposure, identify which wallets would be vulnerable if quantum attacks were possible and develop contingency plans to move assets if needed. Some are exploring time-lock encryption, where transactions could be temporarily encrypted with a short expiration to thwart an attacker from breaking a key during propagation time. These measures are merely stop-gaps. Upgrading the cryptography is the only durable solution.
Regulators and government agencies can meaningfully accelerate the transition by setting clear standards and expectations. Just as banks undergo stress tests, financial infrastructures leveraging blockchain technology should be expected to have concrete quantum transition plans,[17] and new systems like central bank digital currencies (CBDCs) should adopt PQC from the outset. Because the threat is global, international co-operation is key.[18]
Collaborations between central banks successfully demonstrate the feasibility of post-quantum cryptography in financial settings. The French and Singapore central banks (BdF-MAS)[19] recently tested post-quantum encryption for cross-border communication and successfully exchanged information using PQC across continents. This milestone builds confidence around these cryptographic tools in a financial setting. More such pilots could help tremendously – a quantum-resistant blockchain test network among central banks would address practical challenges before they become urgent.
Research gaps remain in efficiency and optimisation. How to efficiently implement lattice-based signatures in resource-constrained environments like smart cards or mobile wallets? How to handle signature bloat when post-quantum signatures can be substantially larger and could negatively impact blockchain throughput? Continued R&D and funding in these areas will pay significant dividends.
Conclusion
The time to begin is now. Blockchain technology is deeply integrated into the financial system, so failing to prepare could have serious consequences. The cryptographic community has been steadily developing quantum-resistant tools. The blockchain sector can leverage this work to fortify itself.
The cost of proactive migration is vastly outweighed by the risk of a quantum-induced crisis, but transition will not be simple. It requires complex upgrades to consensus rules, software and economic incentives to push users toward safer practices. Regulators and policymakers have a bridging role: raising awareness, setting clear standards and co-ordinating industry response. In addition, financial institutions actively investing in or building on blockchain should factor quantum risk into technology risk management now, not later.
The quantum transition for blockchains could closely mirror the web’s upgrade from HTTP to HTTPS. In the 1990s, the web successfully upgraded its encryption to safeguard e-commerce, a transition driven by emerging threats but ultimately accomplished through collective action. Like the Y2K challenge, this requires coordinated, proactive planning. But unlike Y2K, the quantum threat has no known end date, making continuous vigilance essential. From innovation to regulation, the journey to quantum-resistant blockchains will require close collaboration of technologists, economists and regulators. By acting decisively now, we can ensure that trust in blockchain systems remains intact as we enter the quantum age of financial technology.
The time to begin is now. Blockchain technology is deeply integrated into the financial system, so failing to prepare could have serious consequences.
Featured author
Wenbin Wu
Research Associate , Cambridge Centre for Alternative Finance, Cambridge Judge Business School
References
[1] Shor, P. W. (1997). Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. Available at: doi.org/10.1137/S0097539795293172
[2] IOTA Ledger App Documentation: Address Reuse and Chrysalis Update Available at: github.com/iotaledger/ledger-iota-app
[3] Global Risk Institute (2019-2024). Quantum Threat Timeline Reports. Available at: globalriskinstitute.org
[4] IBM Quantum (2025). IBM Unveils 156-Qubit ‘Heron R2’ Quantum Processor. Available at: postquantum.com/industry-news/ibm-heron-r2-quantum/
[5] Gidney, C. (2025). How to factor 2048 bit RSA integers with less than a million noisy qubits. Available at: arxiv.org/abs/2505.15917
[6] Metriq. (2021–2025). Community-driven Quantum Benchmarks. Unitary Fund. Available at: metriq.info
[7] Quantinuum (2024). Quantinuum extends its significant lead in quantum computing, achieving historic milestones for hardware fidelity and quantum volume. Available at: quantinuum.com/blog/quantinuum-extends-its-significant-lead-in-quantum-computing
[8] The Quantum Insider. (2025). Quantum Computing Roadmaps & Predictions of Leading Players. Available at: thequantuminsider.com/2025/05/16/quantum-computing-roadmaps-a-look-at-the-maps-and-predictions-of-major-quantum-players
[9] Cambridge Centre for Alternative Finance (2024). Digital Assets Research. Available at: jbs.cam.ac.uk/faculty-research/centres/alternative-finance
[10] GitHub. (2024). Search code. GitHub REST API Documentation. Available at: docs.github.com/en/rest/search#search-code
[11] BlackRock USD Institutional Digital Liquidity Fund (BUIDL) Available at: en.wikipedia.org/wiki/BlackRock#Tokenized_funds
[12] ‘All Transactions Will Settle On Blockchains Eventually,’ Standard Chartered CEO Says Available at: finance.yahoo.com/news/transactions-settle-blockchains-eventually-standard-151622757.html
[13] Standard Chartered predicts $2 trillion DeFi market by 2028 Available at: analyticsinsight.net/news/standard-chartered-predicts-2-trillion-defi-market-by-2028
[14] Deloitte. (2024). Quantum computers and the Bitcoin blockchain. Available at: deloitte.com/nl/en/services/consulting-risk/perspectives/quantum-computers-and-the-bitcoin-blockchain.html
[15] NIST (2024). Post-Quantum Cryptography Standardization Project. Available at: csrc.nist.gov/projects/post-quantum-cryptography/post-quantum-cryptography-standardization
[16] Buterin, V. (2024). Possible futures of the Ethereum protocol, part 6: The Splurge. Available at: vitalik.eth.limo/general/2024/10/29/futures6.html
[17] NCSC. (2024). Next Steps: Preparing for Post-Quantum Cryptography. Migration timelines and guidance for financial institutions. Available at: ncsc.gov.uk/whitepaper/next-steps-preparing-for-post-quantum-cryptography
[18] European Commission. (2025). Coordinated Implementation Roadmap for the transition to Post-Quantum Cryptography. Available at: digital-strategy.ec.europa.eu/en/library/coordinated-implementation-roadmap-transition-post-quantum-cryptography
[19] Banque de France and Monetary Authority of Singapore. (2024). Post-Quantum Cryptography experiment to enhance communication security. Available at: banque-france.fr/en/press-release/banque-de-france-and-monetary-authority-singapore-conduct-groundbreaking-post-quantum-cryptography